What are you protecting?
To practice cybersecurity risk management, you can start with these steps:
1. Identify your business’ assets
List the types of information, processes, important people and technology your business relies upon.
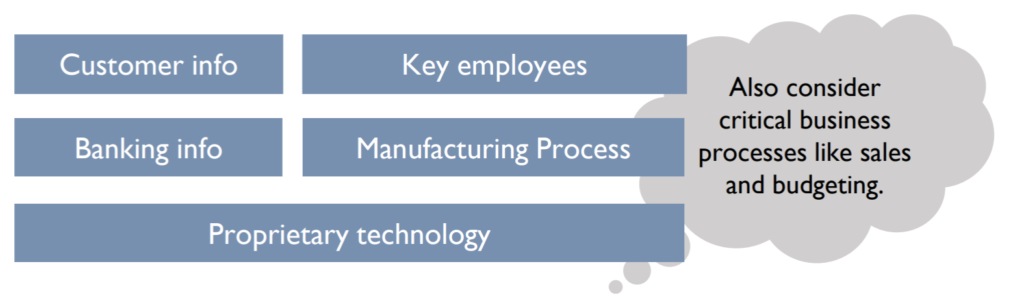
2. Identify the value of these assets

3. Document the impact to your business from loss or damage to these assets
- Consider the impact to your business if each asset were lost, damaged, or reduced in value (e.g., intellectual property revealed to competitors).
- This impact may differ from the asset value determined in step 2.
4. Identify likelihood of loss or harm
- List the threats to each business asset.
- Evaluate the likelihood that the asset may be lost or damaged by the threat(s).
5. Prioritize your mitigation activities accordingly
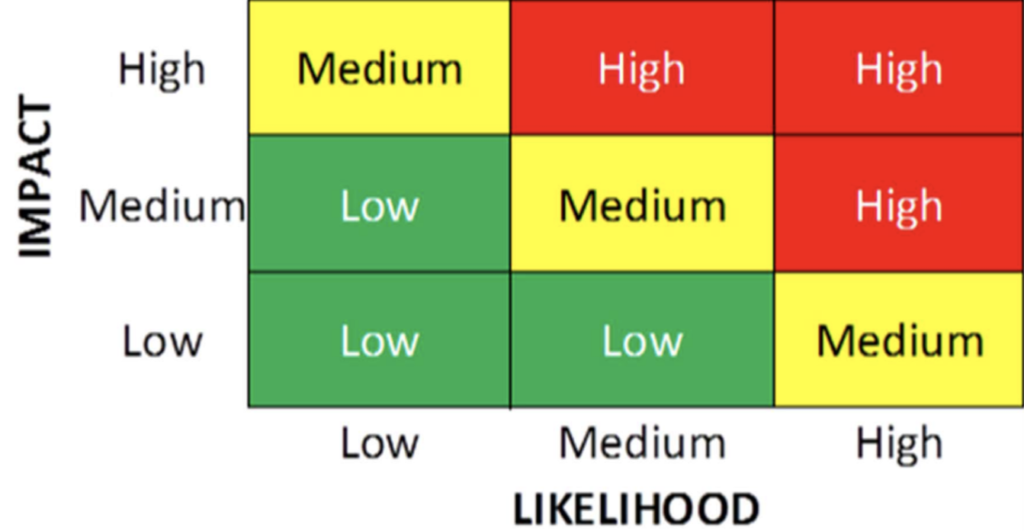
- Compare your impact and likelihood scores. Assets with high impact and/or likelihood scores should be assigned top priorities.
- Identify your priorities.
- Identify potential solutions.
- Develop a plan, including funding, to implement the solutions.
Risk Matrix
Example Risk Assessment
| Asset | Value of the Asset | Impact of Loss/Damage to the Asset | Threats to the Asset | Likelihood of Loss/Damage to the Asset | Prioritization of Protection of the Asset |
| Patient health information | High, due to regulations | High | Hackers, ransomware | Medium | High |
| Devices storing patient information (laptops, servers, mobile devices) | Medium | High | Thieves, malware, phishing | Low | Low |
| Processing patient claims to insurance | High | Medium (can institute manual processes temporarily) | Denial of service, hackers | Low | Low |
| Receiving payments from insurance and patients | High | High | Denial of service, hackers | Low | Low |
| Third party email provider | Medium | Medium | Phishing, malware | Medium | Medium |




